Phishing Assessment
PHISHING ASSESSMENT AND CAMPAIGNS
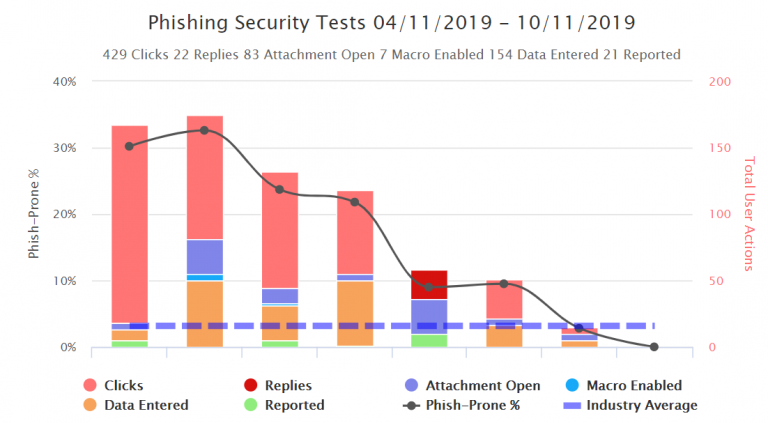
IT pros have realized that simulated phishing tests are urgently needed as an additional security layer. Today, phishing your own users is just as important as having antivirus and a firewall. It is a fun and an effective cybersecurity best practice to patch your last line of defense: USERS
Why? If you don’t do it yourself, the bad guys will.
Here’s how it works
Our Consultants help to provide Public Key Infrastructure Consulting Services and setup your PKI Infrastructure in the right way.
- Conduct interviews with project stakeholders to identify your PKI requirements
- Identify/consolidate PKI use cases (S/MIME, Encryption, BYOD, VPN, AD Login, Wifi Login)
- Identify choice of legacy, PKI platform and key management lifecycle workflows
- Technical Design of your HSM, M of N keys, certificate profile, OCSP, CRL Lifetime
- Review and design architecture
- Propose solution for the identified use cases
- Deliver a design document