Utimaco Hardware Security Module
UTIMACO HARDWARE SECURITY MODULE | HSM PROFESSIONAL SERVICES | SAFENET HSM
WHAT IS UTIMACO HARDWARE SECURITY MODULE
Utimaco is a leading manufacturer of hardware based security solutions that provide the root of trust to keep cryptographic keys safe, secure critical digital infrastructures and protect high value data assets. Only Utimaco delivers a general-purpose hardware security module (HSM) as a customizable platform to easily integrate into existing software solutions, embed business logic and build secure applications. With German precision engineering, tamperproof Utimaco HSM offers scalable performance with the highest level of physical security and self-defense for hostile environments. Tens of thousands of enterprise and infrastructure companies rely on Utimaco to guard IP against internal and external threats and protect hundreds of millions of consumers globally. By building business applications on Utimaco’s hardware root of trust, customers achieve regulatory compliance and the security confidence to focus on their core business.
WHY UTIMACO HSM?
Low operational costs
- Highest performance at an attractive price
- Inexpensive starter models for standard industry applications
- Extensive remote administration
- Efficient key management and firmware updates via remote access
- Automation of remote diagnosis through a network management system using SNMP protocol
- Software simulator for evaluation and integration testing
Capabilities
- Secure key storage and processing
- Extensive key management
- Key storage inside HSM or as encrypted key files
- Smartcard for strong authentication
- “n out of m” authentication
- Separation of duties
- Remote management
- Software simulator for evaluation and integration testing
- Supported OS: Windows and Linux
- Multiple integrations with PKI applications, database encryption, etc.
- All capabilities included in product price
Security, safety, environmental compliance
- RSA, DSA, ECDSA with NIST and Brainpool curves
- DH, ECDH with NIST and Brainpool curves
- AES, Triple-DES, DES
- AC, CMAC, HMAC
- SHA-1, SHA2-Family, SHA3 (as from SecurityServer 4.10), RIPEMD
- Hash-based Deterministic Random Number Generator (DRNG)
- True Random Number Generator (TRNG acc. AIS31 class PTG.2)
- All algorithms included in product price
Cryptographic Algorithms
- FIPS 140-2 Level 3*
- CE, FCC Class B
- UL, IEC/EN 60950-1
- CB certificate
- RoHS II, WEEE
Application Programming Interfaces (APIs)
- PKCS#11
- Java Cryptography Extension (JCE)
- Microsoft Crypto API (CSP), Cryptography Next Generation (CNG) and SQL Extensible Key Management (SQLEKM)
- Cryptographic eXtended services Interface (CXI) Utimaco‘s high performance interface guarantees easy integration of cryptographic functionality into client applications
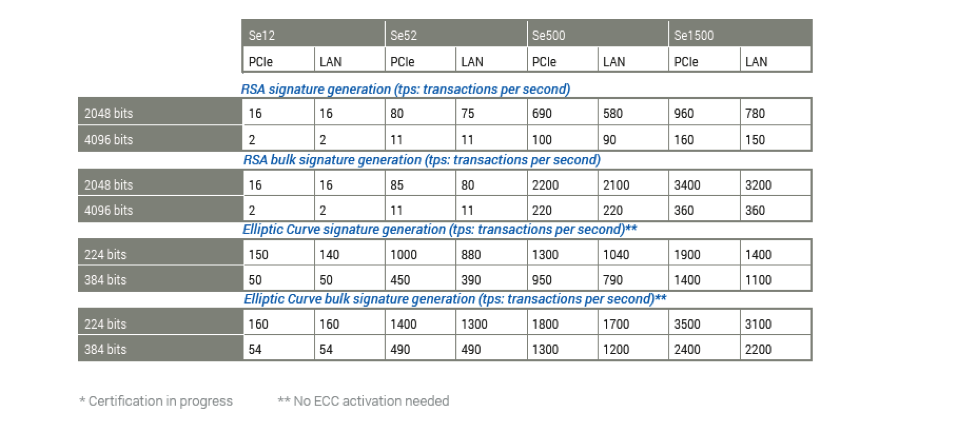
AVAILABLE MODELS AND PERFORMANCE WITH UNLIMITED CLIENT LICENSES